When companies work with data of any kind, data security is immensely important. When those data consist of individual student data, data security takes on a heightened level of importance. Data security simply isn’t sufficient in these cases—it’s incumbent on educators and education service providers to provide data protection. Proactive data protection is crucial, because students are usually too young to grant permission to store and share their data, and parents are often not asked for the right permissions for sharing their children’s information with third parties—or they are not asked for permission at all. Student data are typically entered by school staff (on behalf of students) in tools that the districts choose to use, such as student information systems and gradebooks. Given this reality, we at Education Analytics (EA), along with every other educational service provider, have an obligation to the students that we ultimately serve to protect them and their data.
To do this, we bring the most innovative and up-to-date tools and practices from the Information Technology (IT) and Cyber Security industry into the education space. Without taking this approach, we open the opportunity for hackers and attackers to perform ransomware attacks by illegally accessing student-level data. This also introduces the risk of personal information about students and families leaking outside of our secure servers, which can lead to phishing attempts against students and parents. At EA, we view students and their families as our ultimate stakeholders, so protecting their data means protecting them from these kinds of attacks.
What are our fundamental beliefs about data security and privacy?
Protecting data security and ensuring student privacy is fundamental to our mission and to our business. EA takes protecting the security and privacy of all personally identifiable information and non-personally identifiable information seriously. We have implemented numerous industry best practices and solutions to protect the integrity of the data we collect, including the use of data centers with highly controlled access, routine third-party security audits, restricted employee access to student-level information, as well as data encryption in transit and at rest. The key components of our data security policy include:
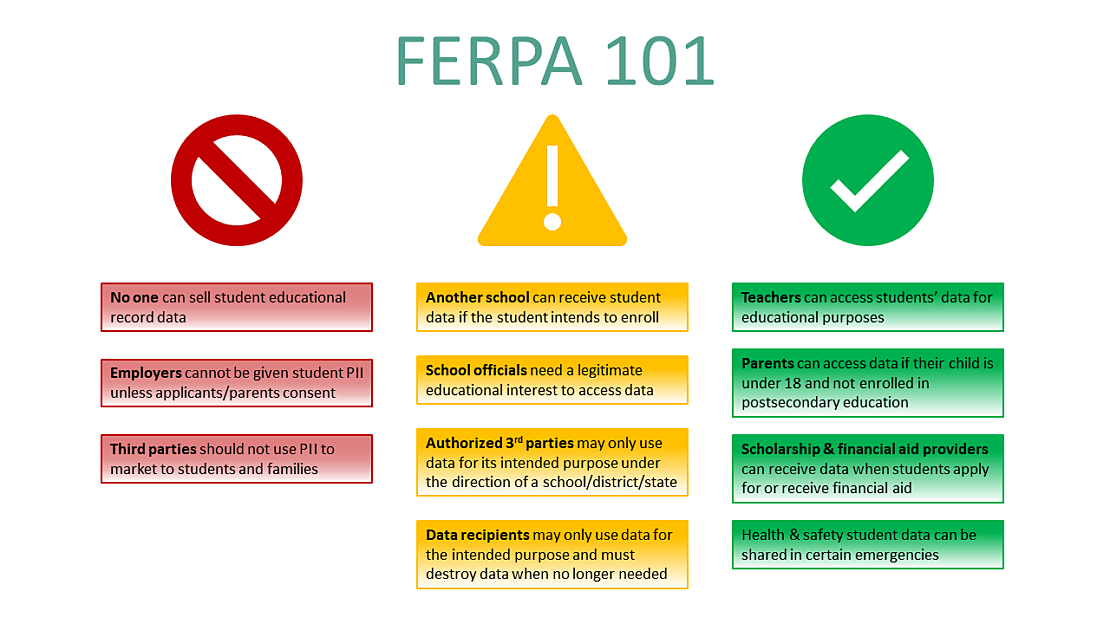
- Ensure strict compliance with the Family Educational Rights & Privacy Act (FERPA; see below), the Children’s Online Privacy Protection Act (COPPA), and all applicable state education laws
- Secure all data in transit and at rest
- Maintain clarity and transparency on data ownership
- Use clearly written out Data Release Agreements (DRA) with school districts, state education agencies, and any other organization that partners with us, so that we clearly communicate the policies in place that govern the use of PII data
What data do we collect and what laws apply to protecting the data?
In general, there are three types of projects we work on at EA: analytics projects, research projects, and web-based dashboard projects. Each of these involves different data sources and data types, and each invokes various applicable data security and privacy laws.
For analytics projects—such as student growth metrics, human capital analytics, and predictive analytics—we collect data elements like student demographic information, assessment scores, attendance data, and Social Emotional Learning survey data, which we typically receive from multiple sources, such as state departments of education, school districts, assessment vendors, and Student Information Systems (SIS). Most, if not all, of the data we receive for these projects are considered Personally Identifiable Information (PII), as they include elements like students’ names, district or state ID numbers, dates of birth, home addresses, or email addresses.
For research projects, we sometimes de-identify the data we receive for analytics projects, in compliance with our partner contracts and DRAs, to be used for agreed-upon research purposes. EA uses de-identification algorithms to prevent reverse engineering of the data or data reconstruction to ensure the highest standards of privacy and security.
For web-based dashboard projects, we additionally collect and analyze data about the usage of the dashboard we create, including user-provided information, communications via the web platform, and information from cookies and log files.
The data elements EA collects are all governed by data security and privacy laws, including the Family Educational Rights and Privacy Act (FERPA), applicable state and federal education laws, such as New York State’s Parents’ Bill of Rights (Education Law 2d), all of which govern the collection, storage, and usage of PII data and student data. For our web-based dashboard projects, any web usage and analytics data are further governed by the Children's Online Privacy Protection Act (COPPA).
As part of our strict compliance with all relevant laws, we train all staff on the required laws and on industry best practices when they are hired at EA, and we provide ongoing professional development for staff so they are kept up-to-date on how best to store, access, and handle data records with an elevated level of security.
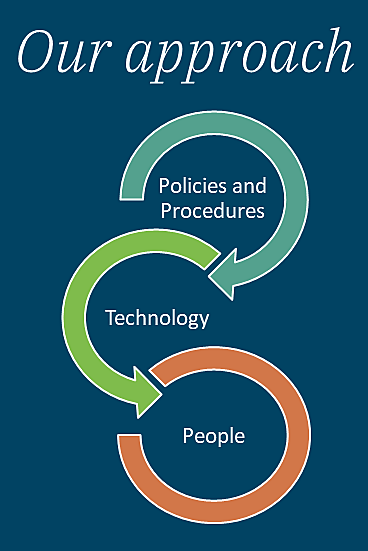
How do we bring these policies and laws into practice?
To get the full picture of how we implement high-quality security practices at EA, we would need to do a deep dive into the many areas of infrastructure building and data workflow that we use at EA. We have a full-time team of IT professionals dedicated to developing and maintaining EA’s policies and procedures, and to delivering best-in-class technology to implement them. Our team also ensures that all staff at EA are not only trained in these policies and procedures, but also understand how to comply with them. These three elements—Policies and Procedures, Technology, and People—make up the key prongs to EA’s approach to data security. Below, we list some of the key strategies that EA uses within these three prongs.
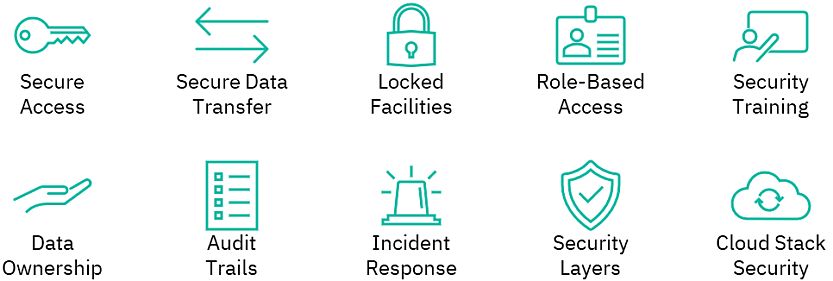
- Locked physical facilities: Our physical facility is locked 24 hours a day, 7 days a week, and entry requires authentication using a key fob with unique codes for each user.
- Security training: Key personnel working with data have federal security clearance and have undergone human subjects and data security training on handling data, FERPA, and other relevant laws governing data use.
- Ensuring secure access: Access to all computer applications and data at EA are managed and authorized at every step using the Windows Active Directory (AD) user ID and high security password procedures.
- Role-based data access: Data access is restricted solely to staff who need such access to carry out the responsibilities of the project based on their role, and staff do not release any data to any unauthorized party as agreed to by signing EA’s non-disclosure agreement.
- Data ownership: EA believes that data are the property of each partner. EA has a data destruction policy which ensures that electronic data stored on the EA file and backup servers are destroyed within the contracted time frames (as determined by our partners) using secure 7-pass DOD wipes. All data received via web usage analytics are considered client-owned, and are handled in a similar high-security fashion as PII data.
- Data Audit trails: EA’s IT systems maintain incident logs and change management logs, which allow for routine audits of IT data security compliance. The security audit process serves to identify, evaluate, and analyze potential threats to, as well as fixes for, EA’s IT system.
- Secure data transfer: All data from our partners are transferred using EA’s secure file transfer solution and stored on encrypted file and backup servers, with access controlled via Active Directory.
- Additional security layers: Single Sign-On (SSO) solutions are a key part of our web-based dashboard solutions, to allow for role-based user access for increased security.
- Cloud stack security: Best practices in cloud technology are implemented on AWS servers to support secure cloud implementations of our web-based dashboarding platforms.
- Incident Response team: In the rare and unprecedented case of data breaches, EA will activate its Incident Response Team. This team will investigate the breach and notify the educational agency owning the data as necessary in accordance with regulations. EA will promptly comply with any inquiries from the partner based upon the partner’s receipt of a complaint or other information indicating that improper or unauthorized disclosure of personally identifiable information may have occurred.
Data security is more than just a set of rules and regulations—at EA, it’s an integral part of the work we do each day. We embrace a continuous improvement mindset that means we set the bar higher the more we learn, achieve, and grow as an organization. How we think about and treat student data is no exception. Without student data, we can’t conduct research and provide actionable data-driven insights to our partners, who work at every level of the educational system to improve student outcomes. If we don’t protect student data at all costs, then we lose our partner’s trust, and in turn, their business.